AWS SSM: Do you really need SSH? How to connect to EC2 using Session Manager
Do you really need SSH? Maybe not!

Secure Shell protocol (SSH) is one of the most common ways to safely administer a remote server across many platforms, using the standard TCP port 22. This is because SSH provides a cryptographically secure connection that allows a user to authenticate, execute commands, and relay input/output from and to a remote server over an unsecured network (The Internet).
For many new AWS users, SSH is the preferred method of accessing instances on compute services such as EC2 or Lightsail. However, after extensive use, or in my case, stumbling across online reports like "Hackers hijacked my account to mine Bitcoin, resulting in a $40,000 monthly bill," one may consider the effort of handling private keys and leaving inbound port 22 open on one's security group to be unnecessarily risky.
How to Connect to Amazon EC2 Using AWS SSM Session Manager
AWS Systems Manager (SSM) is a service that you can use to view or control deployed infrastructure in your account. Among its many capabilities, SSM Session Manager provides secure and auditable node management without the need to open inbound ports, maintain Bastion Hosts, or manage SSH keys, by using the console or the AWS CLI.
Please keep in mind that the steps below describe how to connect to an amazon-linux-2 EC2 instance using a session. This article assumes you already have a similar instance running with an open inbound port 22. If you don't, click "here" to learn how to do so.
1. Create and attach the necessary EC2 Instance Role
Create an IAM role with the policy AmazonSSMManagedInstanceCore and attach the role to your Ec2 instance. This provides permissions for communication between the instance and the Systems Manager API. The AmazonSSMManagedInstanceCore policy enables the instance to use the AWS Systems Manager service core functionality.
2. Verify SSM Agent is running on your Instance
SSM Agent version 2.3.68.0 or later must be installed on the Ec2 instance that we want to log in to using Session Manager. SSH into your instance using the preferred method you have already configured, or use the Ec2 instance connect service on the AWS console. Once inside, proceed with the steps below.
- SSM Agent is installed by default on most amazon-linux AMIs; however, if you need to install it, use this command
sudo yum install -y https://s3.<region>.amazonaws.com/amazon-ssm-<region>/latest/linux_amd64/amazon-ssm-agent.rpm- To verify that the Agent is up and running
sudo systemctl status amazon-ssm-agent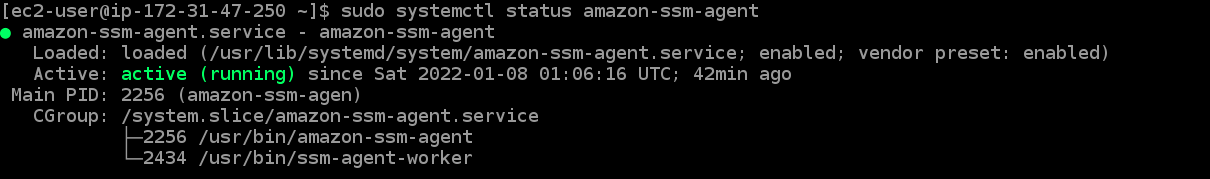
3. Modify your Security Group's Outbound Rules
It is required that the security group of your instance should allow HTTPS (port 443) outbound traffic to enable the SSM agent to connect to some key AWS endpoints e.g ssm.region.amazonaws.com , ssmmessages.region.amazonaws.com. For your preference, you can also configure VPC interface endpoints for this.
Edit your instance's security group to allow outbound HTTPS on port 443. Delete all inbound rules from your instance's security group at this point to close all inbound ports.
4. On your Local Host, install the Session Manager plugin.
The SSM Session Manager plugin is used in conjunction with AWS CLI to run aws ssm commands on your computer terminal, therefore, version 1.16.12 or later of the AWS CLI must be installed on your computer. Click "here" for instructions on how to install aws-cli-v2.
Note: The local host used in this blog is an ubuntu 20.04 desktop
- On your terminal, download the Session Manager plugin package
curl "https://s3.amazonaws.com/session-manager-downloads/plugin/latest/ubuntu_64bit/session-manager-plugin.deb" -o "session-manager-plugin.deb"- Run the installation
sudo dpkg -i session-manager-plugin.deb- Verify the installation status
session-manager-plugin5. Finally, establish a Session to connect to your Instance
Get your instance id from the AWS console, and start a session to your Ec2 instance using the aws ssm start-session command. Make sure to use the region where your instance is deployed when configuring your AWS CLI credentials. Alternatively, you can create a profile for a different region than your default to accomplish this.
The following command launches a session to an instance with the id: i-092c3381dc9f80c0a in my AWS CLI stockholm profile, which is connected to the AWS region eu-north-1.
aws ssm start-session --target i-092c3381dc9f80c0a --profile stockholm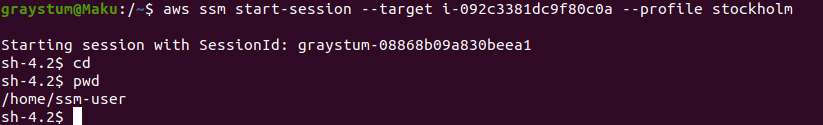
Note: The SSM Agent creates a user account called ssm-user on the instance with root or administrator privileges. This user account's credentials are used to launch sessions. See "here" for information on restricting administrative control over this account.
We're logged in to our instance and in the home directory of the newly created ssm-user, as shown by the pwd command. If we had previously created a user on this instance we could switch to it using su - <username> where <username> is the name of that user.
Voila! We've now started a session to securely connect with our Ec2 instance without using any private keys or leaving any ports open on the network firewall of our instance. I hope you find this information useful. Thank you for your time.
For more information about this topic, see the AWS documentation.
